A brief look at the Juniper Mist Access Assurance (NAC) solution
When you look at the enterprise WLAN industry there is little doubt that it is running full speed ahead towards cloud-managed wireless networks. All the major WLAN vendors now offer a cloud-based management platform. But what about NAC (Network Access Control), should NAC be cloud-based? This was a topic of discussion at Mobility Field 9 with many vendors announcing their cloud-based NAC solutions.
One of those vendors was Juniper Networks who announced Juniper Mist Access Assurance. In 2022 Juniper Networks acquired WiteSand, a cloud-native NAC provider and have spent the last year integrating NAC into their Mist cloud platform.
Configuration
When we look at some on the more established enterprise NAC solutions, we often rely upon solution experts to create complex configurations. However, at Mist the focus has always been on easy or use, implementing enterprise configurations in an uncomplicated way and the Mist NAC solution is no different. The NAC configuration really couldn’t be easier. You create an Auth Policy, configure an Identity provider, and configure an SSID to use the “Mist Auth”.
Let’s take a look at a configuration I created:
Create an Auth Policy:
Below is a screenshot of the Auth Policy I created. This policy will allow network access on VLAN 101 to any user who is in the “wireless users” AD group who has success completed EAT_TLS authentication. Everyone else is denied network access.
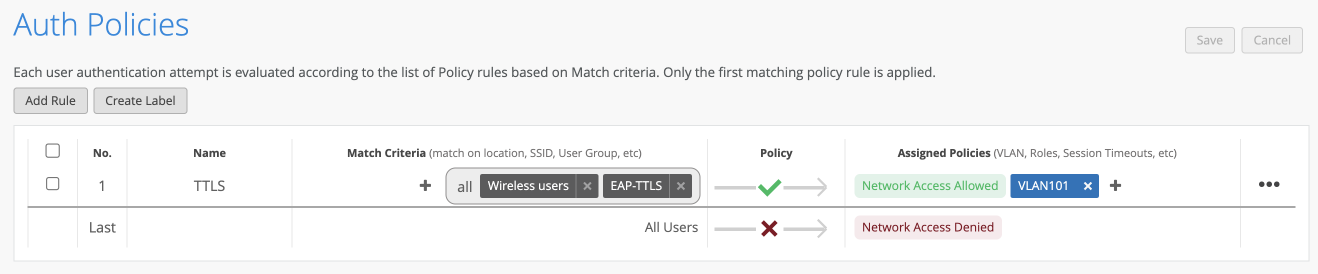
The Auth Policy UI is similar to the WXLAN policy IU and therefore existing Mist administrators should feel comfortable with the configuration of Auth Policies.
Setup an Identify Provider:
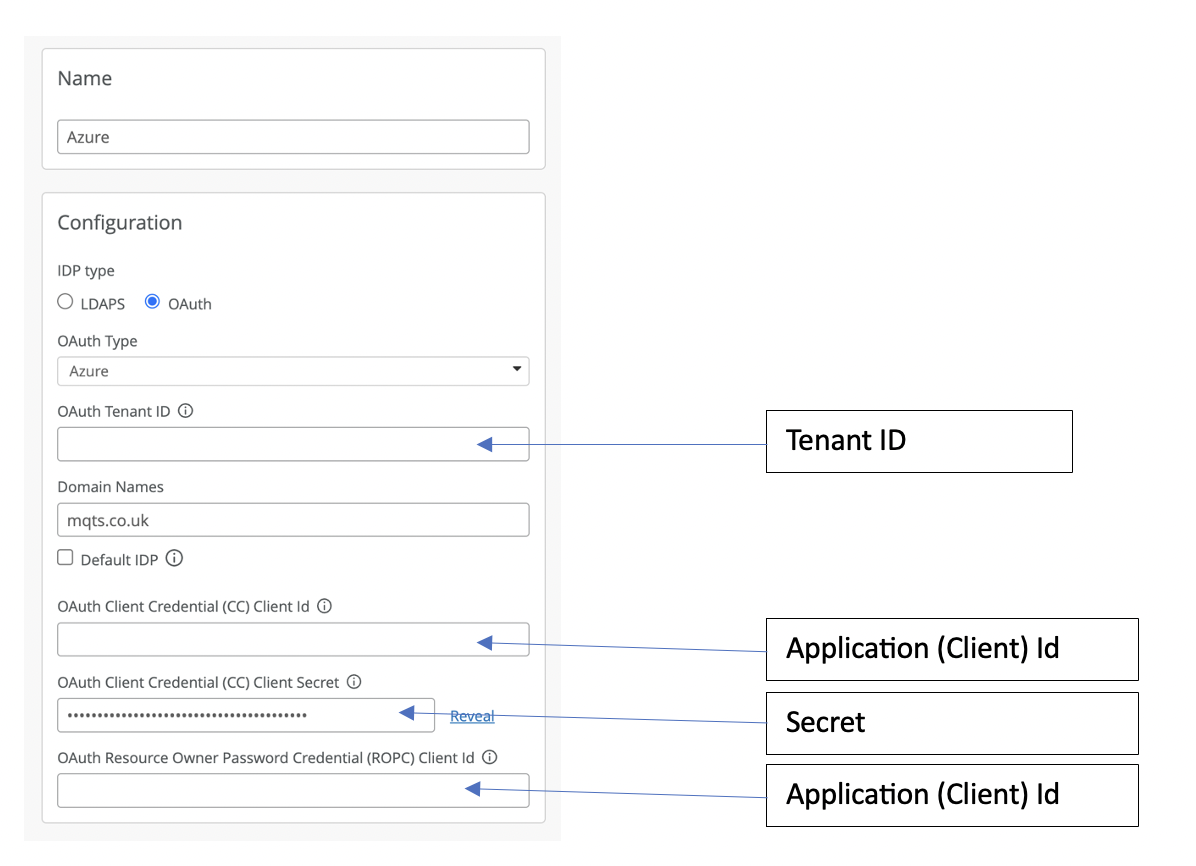
For the Identity provider I used Microsoft Azure AD. Integration with Azure AD requires three pieces of information:
1. Tenant ID – This can be found on your Azue AD overview page. to create an APP requestion for Mist
2. Application (Client) Id – You will need to create a new App registration for Mist, which will generate the Application (Client) ID for you.
3. Secret – Within you new App registration you will need to create a new secret under “Certificates and secrets”.
Once you have these pieces of information you can then configure the identify provider in Mist. Here is how the Mist fields map to the Azure information you have collected.
SSID configuration:
The final part of the configuration is to configure an 802.1X SSID with the Authentication Servers set to Mist Auth.
Cloud NAC concerns
Cloud-based NAC feels like a natural progression in a cloud-managed WLAN world. However, lets first look at two concerns cloud NAC raises.
First cloud NAC solutions go against the traditional advice of keeping your authentication server local to the user, to minimise latency especially for roaming Wi-Fi users. While this may have been a valid concern a number of years ago, today most enterprises implement some sort of centralised NAC solution, such as Cisco ISE or Aruba ClearPass instead of deploying distributed local RADIUS servers. This architecture is possible due to modern-day fast secure roaming protocols such as those defined by 802.11r, where authentication only happens on the initial connection to the network and cached keys are used when roaming between access points. Therefore, cloud NAC solutions implement alongside fast roaming protocols should provide a viable solution.
The second concern cloud-based NAC solution raise is: What if we loss internet connectivity? This is a bigger question then just NAC? A lot of organisations are now implementing a cloud first policy. As our workforces have become increasing mobile and work from home is the new norm having access to our office applications, email and data storage from any location just makes sense. So if all your data and applications are in the cloud, what happens when you lose internet connectivity? Authenticating new users will most likely not be your biggest issue. For the modern-day enterprise with a cloud-first focus maintaining a redundant, high-speed internet connection is critical to their business operations and NAC will be just one of many services with rely upon that availability.
That said a cloud NAC solution is not necessarily the right fit for all. For a variety of reasons some organisations prefer on-premise solutions and for these organisations a cloud NAC solitons would probably not be right choice.
Performance
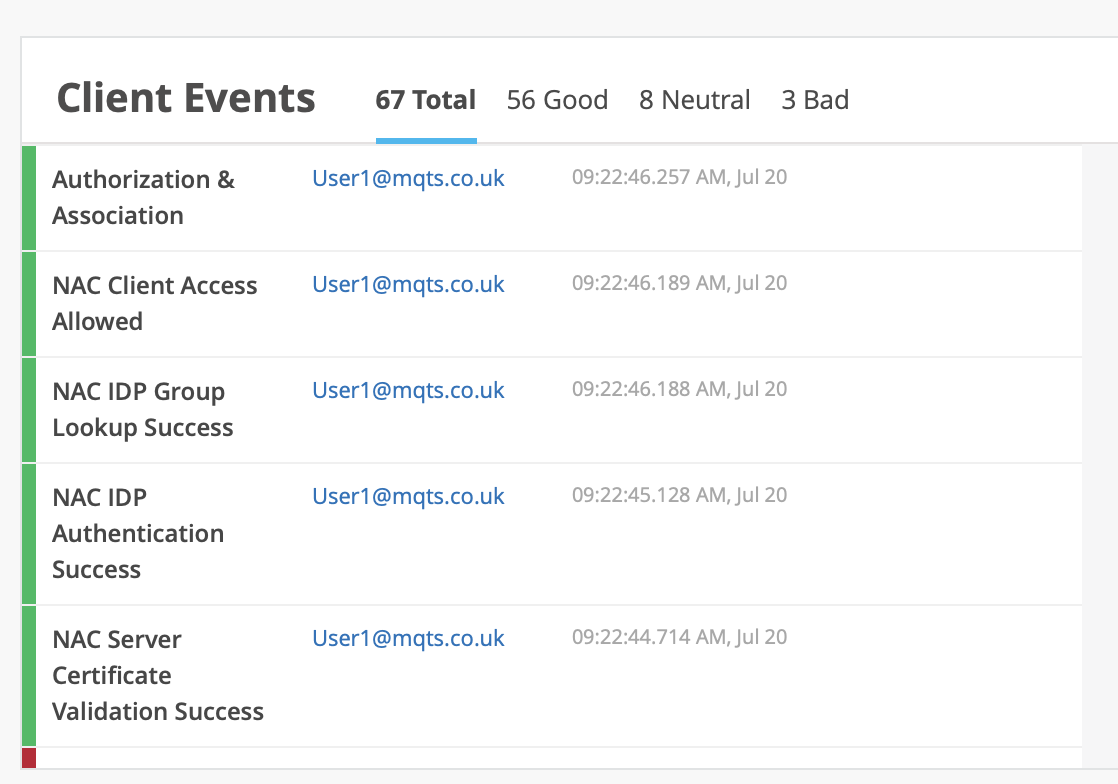
When analysing the performance of a user authentication using Mist NAC and Aruzre AD. I found the total 802.1X authentication could take as long as 2.3 seconds. However further investigation found that most of this time was the Azure AD lookups as see in the events below:
When using certificate-based authentication without the need for a third-party identity provider the Authentication times where greatly improved.
These longer authentication times mean the implementation of fast roaming protocols will be essential when using a cloud NAC solution.
Conclusions
Juniper Mist have done an excellent job in providing a powerful cloud-based NAC solution without the complex configurations which some more traditional NAC solutions suffer from. The Mist team have also done a great job ensuring UI constancy between the Auth Policy configuration and the WXLAN Policy configuration so the configuration should feel familiar to existing Mist Administrators.
The time of a cloud-based NAC 802.1X authentication will vary depending upon the EAP method and third-party identity provider selected. However, these times will generally be longer than using a local authentication server and therefore the deployment of a fast secure roaming protocol such as 802.11r will be essential for a success deployment.

